I have previously demonstrated how to protect wp-admin and wp-login files in word-press website.
I wanted to do more. Something like: Attacking those attackers.
What Crashes Browsers?
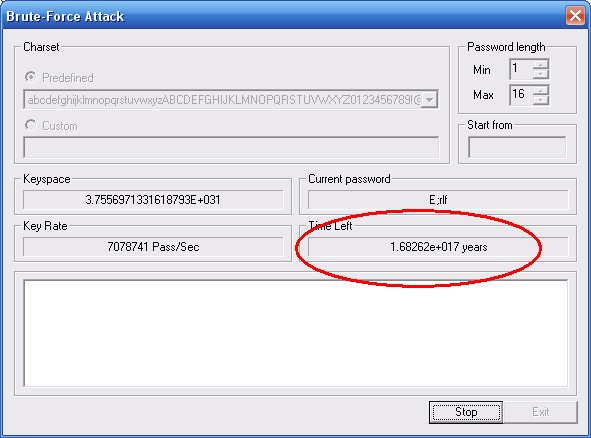
What crashes applications is what hackers call: Buffer Overflow Exploit. Hackers use them to take control of applications/browsers to gain full system access later on. More about buffer-overflows here.
We are not interested to take control of the attacker’s system; Although that will be very ‘cool’ – maybe the next stage? 😉
We are more interested to stop them i.e: Crash their browsers, fuzzing and brute-force tools.
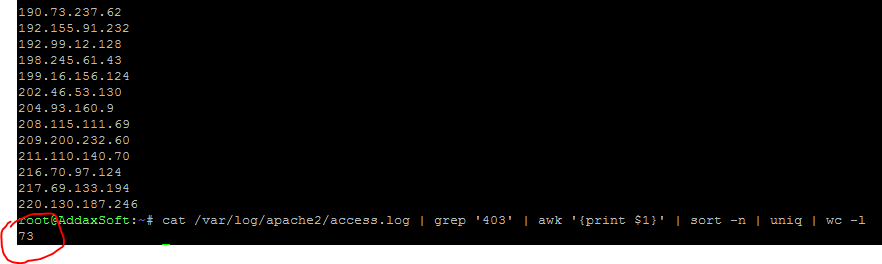
Results.
Amazingly I was able to reduce attacks from 4000~ to around 70 only!
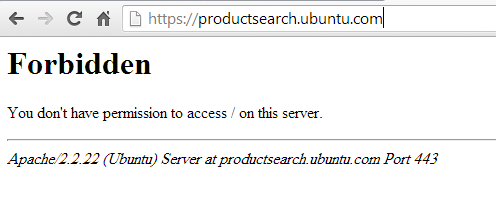
What is happening behind the scenes?
Read More




Recent Comments