I have previously demonstrated how to protect wp-admin and wp-login files in word-press website.
I wanted to do more. Something like: Attacking those attackers.
What Crashes Browsers?
What crashes applications is what hackers call: Buffer Overflow Exploit. Hackers use them to take control of applications/browsers to gain full system access later on. More about buffer-overflows here.
We are not interested to take control of the attacker’s system; Although that will be very ‘cool’ – maybe the next stage? 😉
We are more interested to stop them i.e: Crash their browsers, fuzzing and brute-force tools.
Results.
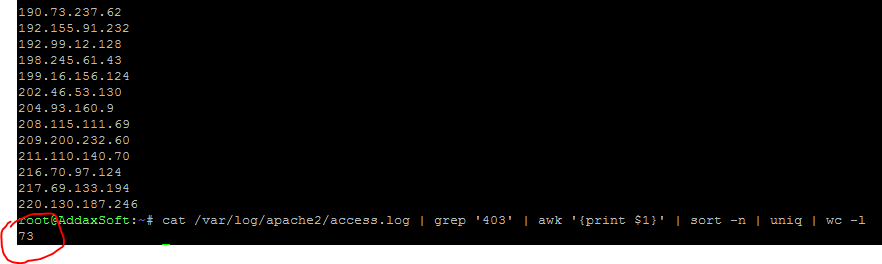
Amazingly I was able to reduce attacks from 4000~ to around 70 only!
What is happening behind the scenes? Browsers are crashing! Remember that browsers were designed to cope with overflows and stress memory usage.
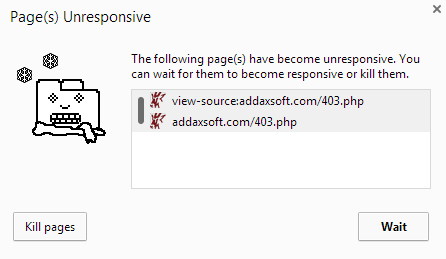
Chrome for instance does not crash, but it will just ‘kill’ the tab – which is enough for me 🙂
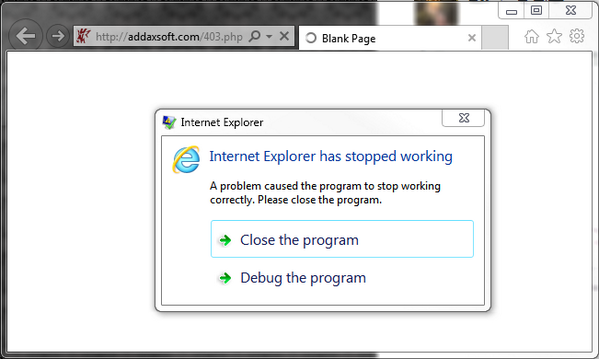
Poor IE, crashes, almost crashing the whole OS with it.
Technique used
I redirect 403 errors to a trap page where PHP scripts runs to create infinite number of div containers, which causes the ‘over-flow’.
Simple yet very effective, which is what Engineering is all about 🙂
Food for Thoughts
I am thinking to try to omit false positives, like what if a normal user tried to genuinely register a new user and got slapped by our 403 page?



Leave a reply