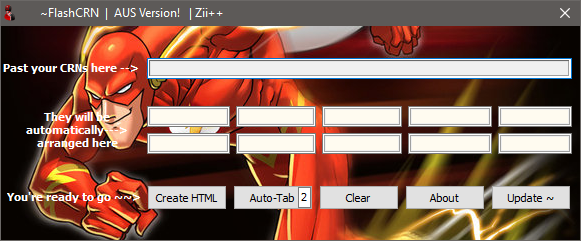
back in 2009 I wrote a tool called FlashCRN because I was very frustrated with people getting my seats in classes I wanted to take simply by going to the dean’s office or talk their way to the registrar desk.
The tool is very simple it writes CRNs into the banner faster than humanly possible; hence it gets you the courses you want from the first try.
Recently a friend of mine mentioned that his brother is using the tool in 2022. To my surprise the tool is made available from generation to generation of students but nobody is aware that it is accessible here on this website by its original author.
You can download the tool from here: FlashCRN.zip
More than 10 years later I think the tool is very poorly written but it does the job and for the sake of authenticity and achievab...
Read More





Recent Comments