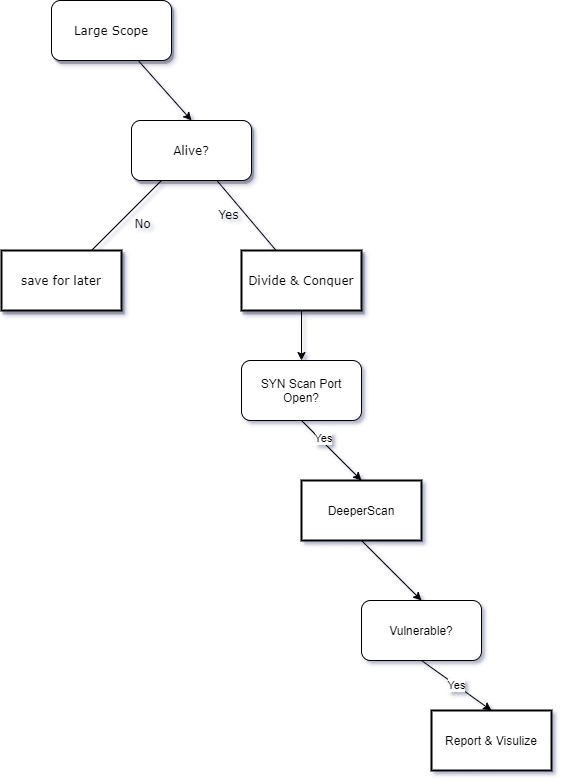
If you follow me on Twitter @xxByte you must have seen the tweets about scaning a large scope of IPs and how did I approach that.
The goal: To scan all TCP ports (0-65536) of ~800 IPs spread across Europe and detect any low hanging fruits using automated tools or manual assessment in the most efficient way with the least resources needed.
The approach:
Let’s first do some math. Scanning 65536 TCP ports on 800 IPs means:
65536 x 800 = 52428800. That’s 52428800 SYN packet out and waiting for a SYN ACK reply packets in total.
To have the rest of the project requirements we need to scan each open port with deeper script scan and version detection scan, which means even more packets.
At such scale we cannot afford to script scan blindly all TCP ports...



Recent Comments