You’ve seen before how I got targeted by thousands of brute force attempts and how I mitigated the attacks earlier in this post; however, I wanted to do something better and more efficient. A filter at the firewall to block all these attempts from even establishing a basic TCP connection with the HTTP server.
The Problem
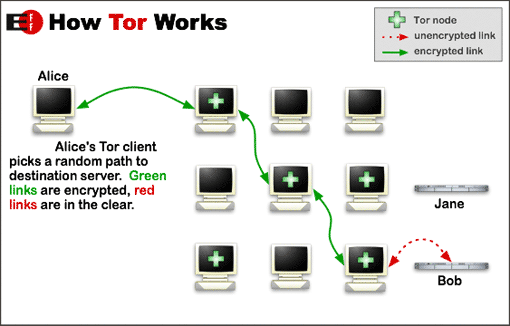
One major problem is that these attempts were not coming from a single IP address. Attackers will use TOR to hide themselves and to have different IPs to over-come the first obstacles that is: blocking the attacker’s source IP address.
Init Solution
According to this answer here, there is a script by TorProject that can give you a list of Tor Exit Nodes to your server. For example I can get a list of all exit nodes IP addresses using this url: https://check.torproject.org/cgi-bin/TorBulkExitList.py?ip=23.226.135.25&port=80
Using this list one can dynamically block all Tor traffic for an amount of time – as long as the attack is going then switch the filter off to allow people who use Tor as a way to protect their privacy (although you can still sniff all data if you’re the Exit Node – read this article for more details on that: Tor: Exploiting the weakest link)
I will write a script to do that soon. Stay tuned. (Thank you Python!)



Leave a reply